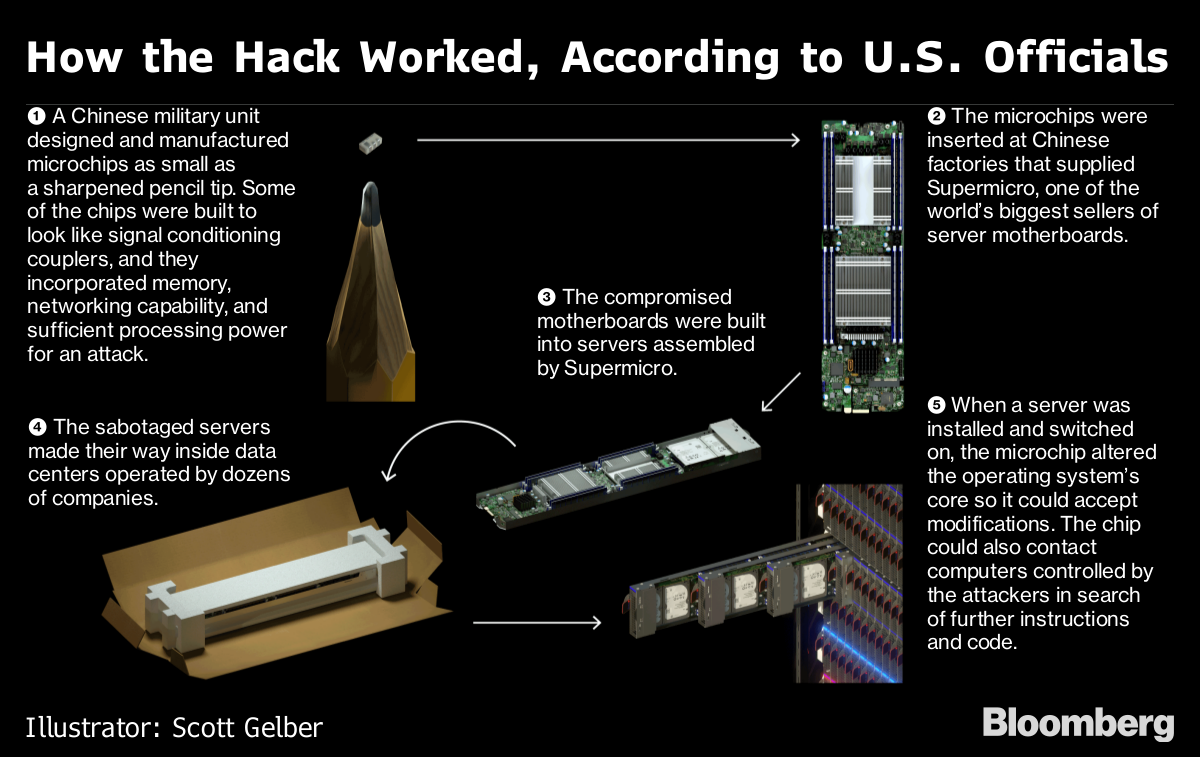
A major US telecommunications company discovered manipulated hardware from Supermicro in its network and removed it in August, fresh evidence of tampering in China of critical technology components bound for the US, according to a security expert working for the telecom company.
The security expert, Yossi Appleboum, provided documents, analysis and other evidence of the discovery following the publication of an investigative report in Bloomberg Businessweek that detailed how China’s intelligence services had ordered subcontractors to plant malicious chips in Supermicro server motherboards over a two-year period ending in 2015.
He said that unusual communications from a Supermicro server and a subsequent physical inspection revealed an implant built into the server’s Ethernet connector, a component that's used to attach network cables to the computer.
He claims to have seen similar manipulations of different vendors' computer hardware made by contractors in China, not just products from Supermicro. “Supermicro is a victim -- so is everyone else.”
Appleboum said his concern is that there are countless points in the supply chain in China where manipulations can be introduced, and deducing them can in many cases be impossible. “That's the problem with the Chinese supply chain”, he said.
Supermicro, based in San Jose, California, gave this statement: “The security of our customers and the integrity of our products are core to our business and our company values. We take care to secure the integrity of our products throughout the manufacturing process, and supply chain security is an important topic of discussion for our industry. We still do not know any unauthoriszed components and have not been informed by any customer that such components have been found. We are dismayed that Bloomberg would give us only limited information, no documentation, and half a day to respond to these new allegations.”
Supermicro said after the earlier story that it “strongly refutes” reports that servers it sold to customers contained malicious microchips. China's embassy in Washington did not return a request for comment Monday. In response to the earlier Bloomberg Businessweek investigation, China’s Ministry of Foreign Affairs didn’t directly address questions about the manipulation of Supermicro servers but said supply chain security is “an issue of common concern, and China is also a victim”.
Appleboum determined that the telecom company's server was modified at the factory where it was manufactured. He said that he was told by Western intelligence contacts that the device was made at a Supermicro subcontractor factory in Guangzhou, a port city in southeastern China. Guangzhou is 90 miles upstream from Shenzhen, dubbed the `Silicon Valley of Hardware,’ and home to giants such as Tencent Holdings Ltd. and Huawei Technologies Co. Ltd.
The tampered hardware was found in a facility that had large numbers of Supermicro servers, and the telecommunication company's technicians couldn’t answer what kind of data was pulsing through the infected one, said Appleboum, who accompanied them for a visual inspection of the machine. It's not clear if the telecommunications company contacted the FBI about the discovery.