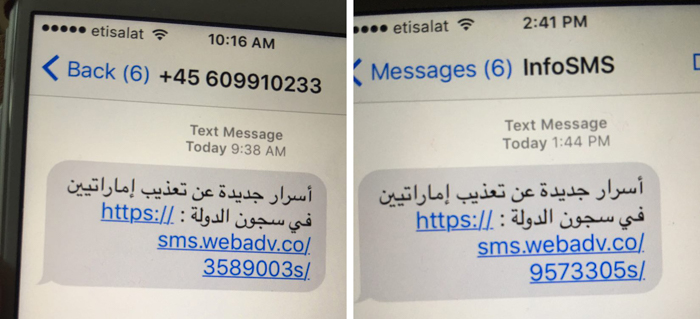
Image source: CitizenLab.org
Canadian security research organization CitizenLab reports that award-winning activist Ahmed Mansoor, based in the United Arab Emirates, received SMS messages on his phone on August 11th and 12th containing linkbait promising him information and “new secrets” about detainees being tortured in UAE jail cells. Instead of clicking the link, he forwarded the message to CitizenLab and the organization was able to confirm not one, but three highly suspicious exploits in iOS, including a government-exclusive “lawful intercept” product.
Messages linked to NSO Group “Pegasus” spyware product
A collaborative investigation between CitizenLab and Lookout Security discovered a chain of zero-day exploits that “would have remotely jailbroken Mansoor’s stock iPhone 6 and installed sophisticated spyware.” In particular, the link in question would have executed arbitrary code through the WebKit webpage layout engine to gain access to the iOS kernel and execute code from there.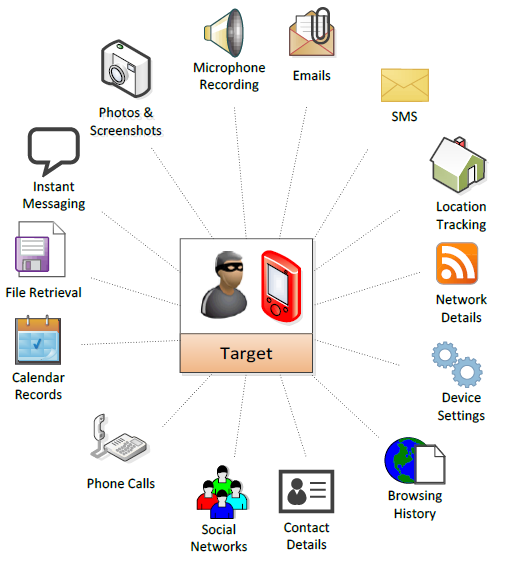
Image source: CitizenLab.org
The suspicious text messages in question linked to a spyware product belonging to NSO Group, a Tel Aviv-based software company owned by a San Francisco-based equity firm that created and has purportedly been operating a spyware program called “Pegasus” since 2010 at the company’s inception. While the evidence in Mansoor’s case is documented by two security firms, it does hint that NSO has been not only been deployed for combating terrorism and spies, but conversely has targeted citizens acting against government special interests.
A list of domain names registered by NSO, several other countries could have been targeted as well including Turkey, Israel, Thailand, Qatar, Kenya, Uzbekistan, Mozambique, Morocco, Yemen, Hungary, Saudi Arabia, Nigeria and Bahrain, according to a Forbes report.
Once infected, Mansoor’s phone, or any iOS device in general, would become susceptible to having its applications, calls and messages monitored, its internal camera and microphone hijacked for monitoring of any audible and visual information in the vicinity, and having its movement and geolocation data monitored among other bits of information. The researchers later discovered that Mexican journalist Rafael Cabrera had been targeted as well.
CitizenLab and Lookout are calling the three exploits in question the “Trident Exploit Chain” and has listed them as CVE-2016-4657, CVE-2016-4655 and CVE-2016-4656 on the international common vulnerabilities database.
Apple patched the three zero-day vulnerabilities ten days later and is now advising all iOS device owners capable of receiving its latest iOS 9.3.5 software update to install it sooner rather than later.




